
Every hour there are more data breaches than there are citizens living in Bern, the capital of Switzerland. Data Breach Index records over 250,000 data breaches every hour — a staggering number.
These breaches affect a combination of corporations, governments, and individuals. The data being stolen can be anything from usernames and passwords, to credit cards and healthcare records. Which data is the most in demand? And which data will do the most damage to you if stolen? Let’s look into this here, in the last part of the Trezor Data Privacy Series.
Why do the hackers hack?
Money
Most hackers simply want to generate profit. They can make money by stealing private information like a credit card or login details, and withdraw money from your accounts by themselves; or they can resell this information to another entity on the internet. The deep web is filled with offers to buy and sell personal information from all around the world.
In the last few years, it has become common practice to hack someone’s devices and encrypt data on the device. In this case, the hackers will make sure that the victim knows exactly what’s going on and that they’re going to have to pay a ransom if they want their valuable files back. If the victim does not pay, the data will remain encrypted or delete themselves after a period of time set by the perpetrator.
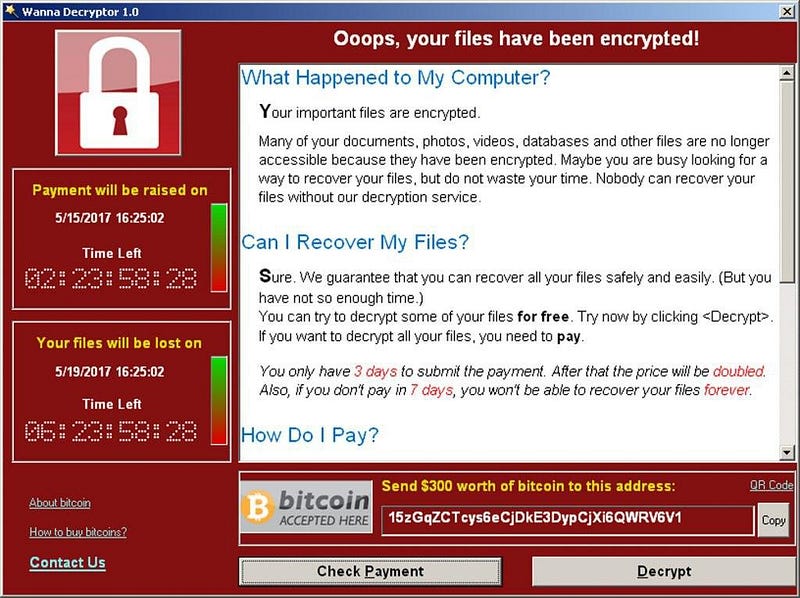
Personal reasons — political motivation, ideology, and hacktivism.
Not all hackers are in it to make money. There are self-proclaimed vigilantes who work to expose terrorist groups, child abuse, or the practices of oppressive regimes. One of the best-known hacktivists in the world is Edward Snowden, who is currently on the run after leaking data from the National Security Agency. He released the information that the NSA had been spying on millions of American citizens without their knowledge, along with more disturbing information that you can find in this Github collection.
To make a point or disrupt the services.
Some hackers just want to show off their skills. There is a group of hackers who have no intention of making money or stealing data. They just want to send a message. One such hack is the well-known Ashley Madison data breach, where hackers obtained and publicly exposed the profiles of all 32 million registered users. Ashley Madison is a website that calls itself a platform that enables and encourages extramarital affairs.
The Impact Team group behind this hack called this website and the behaviour of its users immoral. They made sure that everyone affected was well aware of what happened, exposing their affairs to families and the public.

What happens to your data after they’re stolen?
Once a hacker obtains your data, there are several things they can do. One of the most common procedures would be to scan the data for important or valuable information such as login details, payment information, private photos, or messages and e-mails. Afterwards, they will decide whether they’re going to use these files themselves or if they’re going to sell them to a third party. In most cases, the hacker will not use the data, but instead will sell them to a third party, often called a “broker.” By selling the stolen information, they’re reducing the risk they’re facing compared to the risk of using the data by themselves.
A price for the stolen data is set based on the potential for profit. Information about lucrative accounts is predictably more expensive than the data of your average Joe. If the stolen data comes from a government or military personnel, the cost can grow to staggering heights.
Credit cards and payment details.
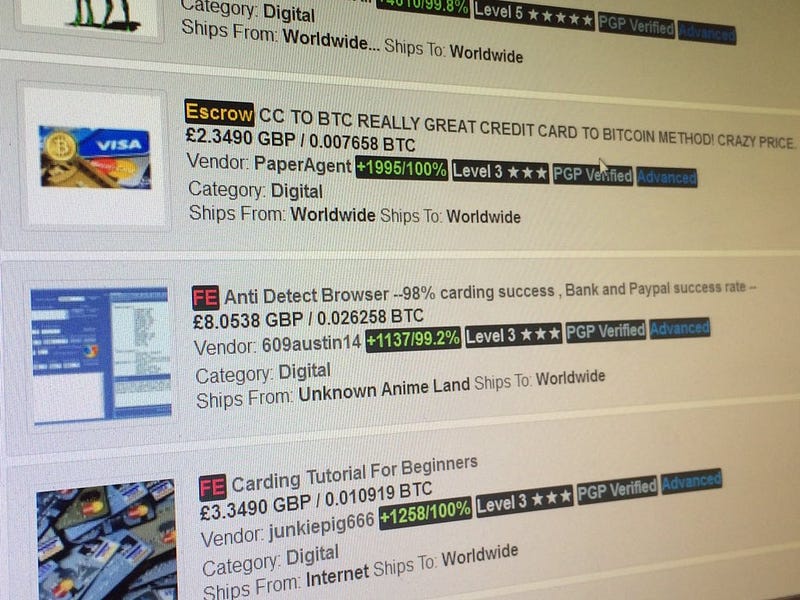
Credit cards and payment details are the most sought-after marketplace goods on the deep web. The procedure of clearing funds from your account is not too complicated. In most cases, a “broker” will buy the card details from the marketplace and resell them to a “carder.” Carders are people who will then proceed to get as much of your funds out as possible before you or your bank finds out. They can replicate the card by printing one themselves, but more often they will use them for a gift card shell game. This means that the carder will use your card details to buy online gift cards for Amazon or other retailers, then use these cards for purchases.
In most cases, they will purchase electronics because they’re in demand almost everywhere in the world and can be easily resold with practically zero risks involved. Using these electronics or other goods to purchase drugs is a fairly common practice too.
When it comes to credit cards, the risk of losing your funds is very small compared to the risk involved in using debit cards. Debit cards are more common in Europe than in the US, and they’re extremely valuable goods because they’re directly connected to your checking account. In case of credit card fraud there are several procedures and insurance to protect you, so in most cases, the funds can be recovered or paid by the insurance or credit card company — but if your debit card funds are stolen, not much can be done about it.
Names, e-mail addresses, photos, date of birth and other personal information.
These data are not really valuable for the black market since they’re widely available on the internet. Your name, e-mail address, and often much more information can be gathered just by going through your social media. We post this data voluntarily, and without adequate privacy settings they can easily be stolen and used against you or for profit.
In recent years there has been a huge growth in blackmailing, extortion, or ransom. Hackers will obtain your data and then threaten to release them to the public. This is a more common practice used against women, where they will be blackmailed with private photos or messages and asked to pay the ransom or have their reputation ruined with one click of a mouse. These data are extremely valuable if the victim is a prominent or powerful figure.
Recently, the richest man in the world was caught in such a spiral when the National Enquirer allegedly threatened to release the communication and photos exchanged between Jeff Bezos and his mistress.
Personal documents, insurance numbers, and tax details.
This type of information is undoubtedly the most valuable. With the ever-increasing amount of know-your-customer (KYC) procedures, the risk of these data being stolen is increasing as well. Trading platforms, subscription services, and retailers commonly require their users to complete a KYC procedure, where a set of personal documents such as passports, driving licenses or IDs is used to verify the identity of the user.
Sometimes this procedure might even require the user to take a selfie with a specific text written on the paper to further strengthen the verification process. But what happens if a database filled with KYC information gets into the wrong hands? KYC contains everything a hacker needs to steal your identity and commit fraud.
By having your passport paired with your selfie in their hands, they can register for exchanges and wash trade hundreds of thousands of dollars in your name. They can claim your tax credits, your insurance claims, or in some cases even go as far as opening a bank account in your name and getting a loan.
There is no certain way to verify whether any of your data has been accessed by a malicious third-party, but there are some handy websites that you can use to check this up to a point. A very useful website called Have I Been Pwned can check if you’re registered on a website that experienced a data breach and offers some tips on how to recover and protect your data. Unfortunately, there’s no way to prevent this as long as you are not in charge of the security of your data. Corporations spend excessive amounts to increase their security and train their staff, but that still might not be enough. Demand to know how, where, and by whom your data are used and protect your privacy.
Your data are online and so is your life. Every single interaction online could place you at a tremendous risk of losing money, losing your personal information, or damaging your life and reputation. Always stay cautious and vigilant and do everything you can to protect your digital identity and privacy.
About Us
SatoshiLabs is the innovator behind some of the most pivotal and influential projects involving Bitcoin and cryptocurrencies: mainly Trezor, the world’s first cryptocurrency hardware wallet, and CoinMap.org, the primary resource for bitcoin-accepting venues.
Our Trezor Model T is the next-generation hardware wallet, designed with the benefits of the original Trezor in mind, combined with a modern and intuitive interface for improved user experience and security. It features a touchscreen, faster processor, and advanced coin support, as well as all the features of the Trezor One.
The Trezor One is the original and most trusted hardware wallet in the world. It offers unmatched security for cryptocurrencies, password management, and serves as the second factor in Two-Factor Authentication. These features combine with an interface that is easy to use whether you are a security expert or a brand new user.